I2P Performance Statistics
I have tested i2p ....
It works, but the performance, anonimity and reliability are very questionable…
TL;DR
To put it short
- Tested 3 types of deployments to measure how they work as proxies (very similar)
- Tested 3 types of hidden service deployments (i2p+ was the best)
- Flood participation is not affecting i2p network performance, but increased resources consumption.
I2P is slow. One ping takes 5-10 secs. And it’s not garanteed that it doesn’t time-out, even if you have good connection.
Shortly what it is
I2P is a network protocol on top of IP, it uses both TCP and UDP, both IPv6 and IPv4.
The main idea is like TOR - to pass the network packets enctipting them on the fly, so
- the node that passing the packet doesn’t know what’s inside
- node that received the packet doesn’t know original sender.
I2P doesn’t have standard way to view “big internet” (clearnet), there are outproxies, but come on… TOR is much better at this. What i2p has is “hidden servies”. Theoretically those services doesn’t know who calls them and users do now know which node each service is located.
Services could be any standard internet program - IRC server, web server with whatever is hosted there, REST API, XMPP or mail server.
And there is not a lot of services there. Approx 200 sites? Or 300?
Purpose, Way, Moral and Legal aspects.
I could see two motivations to host hidden service
- Enforce (make sure) of own anonymity and privacy
- Escape direct eye of Big Brother - not all people live in democratic countries, some tyranical governments oppress and repress whoever they can. But into this bucket (“escape”) I would put any illegal activity. It is just a motive.
Moral and legal aspects are complicated. My view (I’m not a legal expert, so don’t take it as an advice):
People have [moral] right of privacy. They have a [moral] right to say “F.U. It’s none of your business”. They have a [moral] right to be … let’s say … not happy, when some programs or mobile phones are publishing their location, satellites are taking photoes of their backyards and publishing those on google street view, and governments are ignoring this activity and not-happiness. At the same time government has AFAIK [legal] right to invade people’s privacy, there are some conditions, sometimes. For instance in Australia police constable can demand you to unlock your mobile phone, which has huge moral implications. See history of Monica Smith who was some way demanded to unlock her phone, where police would get contacts of pro-freedom protestors. (Those were the days of COVID lockdowns in Melbourne, the hardest in the world). Police pulled back, but Monica then risked jail time for not compliance.
Anonimity is another big aspect of people’s lives. My view is that surveilace and deanon is too frequently used only for doxxing, privacy invasion and bullying. And better to have clear rules and procedures when anyone allowed to use it.
Performance
OK. Here we go.
I have measured how long it takes to complete the ping. (HEAD {site}.i2p)
Below is the response delay spread.
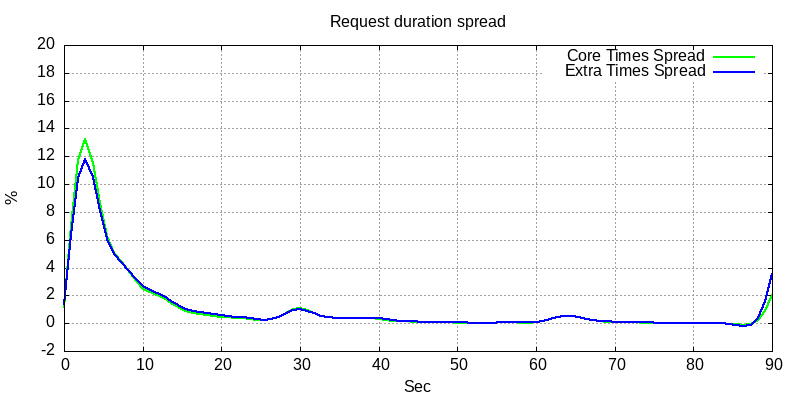
This spread graph shows that expected call duraion would be around 5secs.
I did set timeout to 90 secs, and as you see some requests didn’t complete at all. 30 secs and 60 secs I guess are some service-side or router-side timeouts.
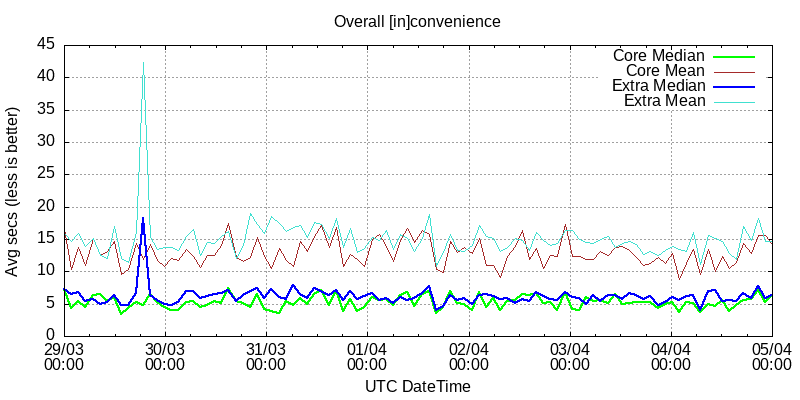
Core sites are well-established sites http://idk.i2p/, http://zzz.i2p/, http://identiguy.i2p/, http://333.i2p/, http://i2pforum.i2p and similar, total 25 of those. Group Extra - set of other 100+ sites.
I assumed that core sites’ owners know what they are doing, and indeed their sites performance is better then from group extra. But the difference is not huge - just 1 sec (~5sec vs ~6sec median call duration). AND! core sites were still timing out occasionally, as you see on the first graph (request duration spread).
Below is the proxy type usability graph.
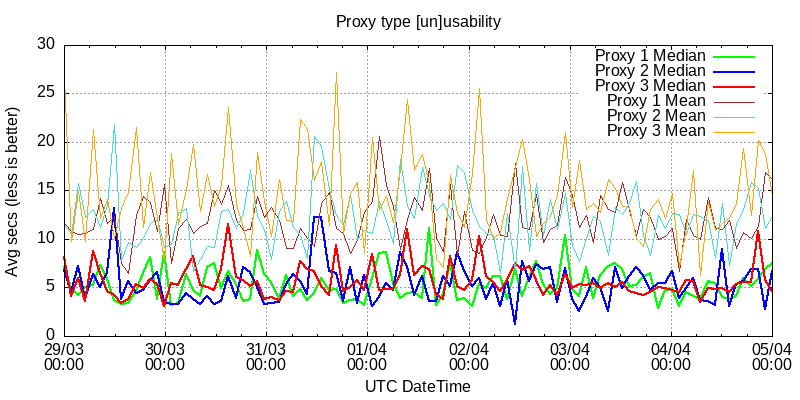
Measured ping durations of sites from Core group from different proxies. I2P+ on one and I2Pd on two different deployments are showing pretty similar results.
Now service hosting suitability.
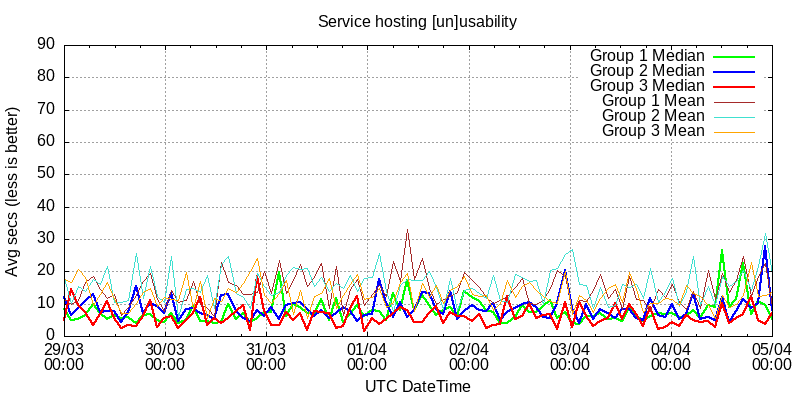
The thick red one here is I2P+.
Anonimity
There were 4000-10000 routers online, their public IP addresses are well visible. So we can not talk about huge anonimity here.
Resource consumption
I2Pd in my experiments consumed ~130MB RAM + ~7% CPU.

I2P+ was consuming ~350+MB RAM + ~70+% CPU.
In I2P+ config I have increased RAM allowance a bit, hoping it would perform better. So, here we are.
Flood participation in my experiments was not affecting i2p network performance, but increased CPU load approx. +20%.
So if you planning hosting I2Pd - 1vCPU+512MB would do, I believe. And for I2P+ - 2vCPU+1GB at least.
The feeling
It is like a Fido, BBS and ol good times. When the net is so small that almost everyone knows each other, just by nicknames.
It is slow. And empty.
But the feeling is so analogue.

